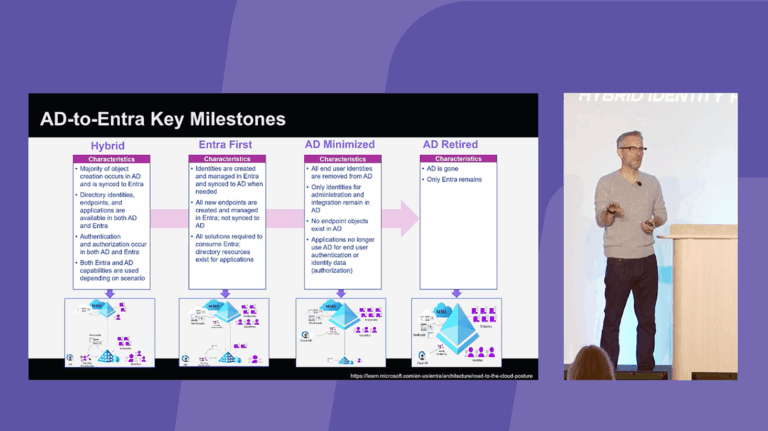
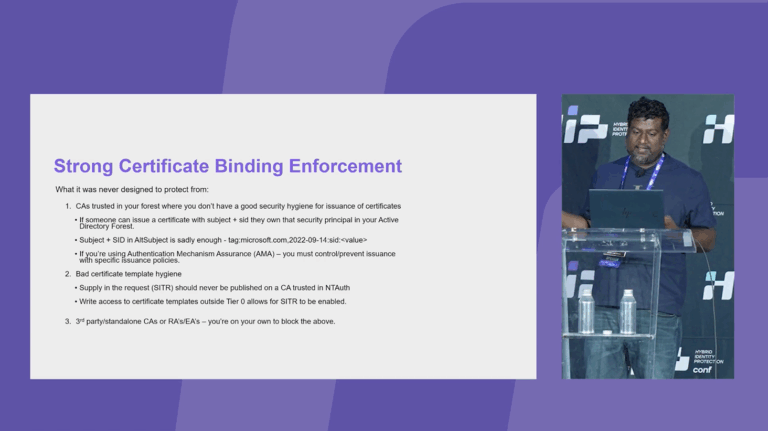
Stories from the Field: Practical Steps to Accelerate Response and Minimize Downtime After an Active Directory Attack
It’s no secret that the identity system is the primary target for cyber criminals. By compromising hybrid AD/Entra ID, the primary identity store for 90% of organizations worldwide, cybercriminals can disrupt business operations and extract sensitive data that they can use to demand ransom. What’s less understood is what happens inside the organization after Active Directory is attacked. What services and apps will go down? How will the IT and security teams communicate with each other? How can a known good AD backup be identified and accessed? Where is the response plan stored and does anyone have access to it when systems are down? Anyone have the cyber insurer’s contact info?
In this lively conversation among top experts In Identity Forensics & Incident Response (IFIR), we’ll unpack real-world identity attack response timelines: What goes sideways and how you can prepare for the worst.