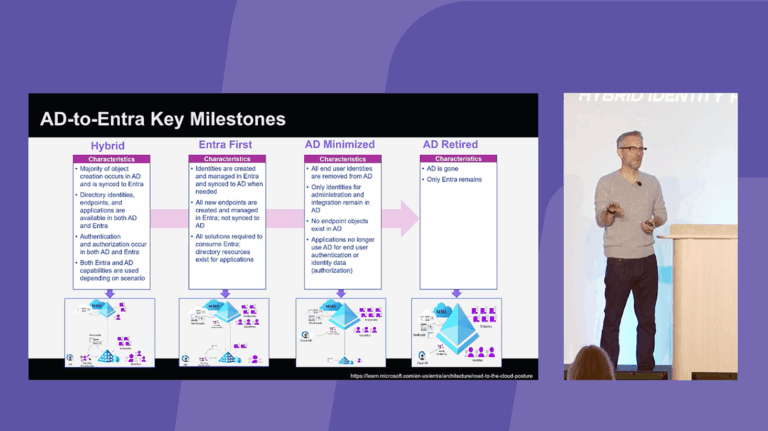
Password Sprays & Token Plays: The Art of Staying Secure in Microsoft Entra
From token theft on unsecured endpoints to Adversary-in-the-Middle (AiTM) phishing and illicit consent to malicious applications, threats against Microsoft Entra are continually evolving. This session examines the latest attack techniques and emerging trends targeting identities in Entra environments. We’ll explore multi-stage attack chains, sophisticated persistence techniques—and automated attack disruption capabilities that can help limit lateral movement, reduce the blast radius, and provide security teams with high-confidence insights. Through detailed analysis of real-world attack scenarios, you’ll gain actionable and efficient strategies to mitigate your risk of compromise.
October 16, 2025
See Other Session
Sign Up for Email Updates