End the ESCape Clause: Combatting AD CS Vulnerabilities
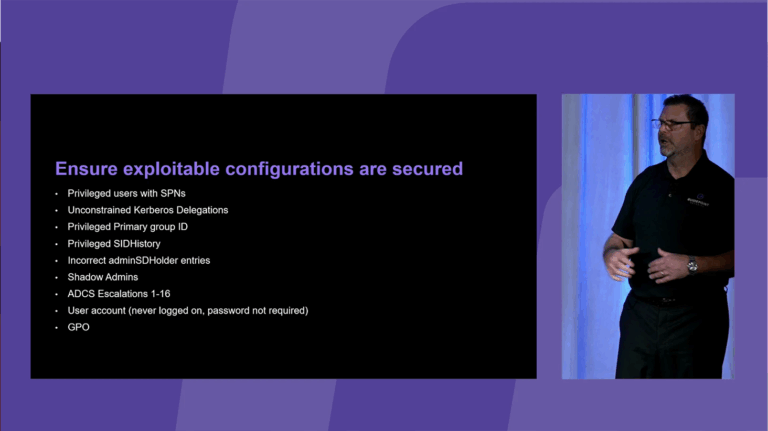
Explore a crucial but under-discussed threat: the combination of seemingly low- or medium-severity Active Directory Certificate Services (AD CS) issues that, when used in tandem, can lead to full Active Directory forest compromise. AD CS is a powerful and often-overlooked avenue for privilege escalation in enterprise environments. While individual misconfigurations (especially the well-documented privilege escalation paths commonly known as ESCs) are widely understood in both the offensive and defensive security communities, a significant gap remains in understanding how these vulnerabilities can be linked together to escalate risk. Based on original research, lab testing, and information gleaned from real-world AD security assessments, this session features live demonstrations of at least three distinct ESC combinations that illustrate different paths from typical user access to Domain or Enterprise Admin. Learn why defenders often miss the bigger picture by analyzing AD CS configurations in isolation and discover ESCalator, a PowerShell-based tool designed to help both red and blue teams understand AD CS exposure by quickly surfacing escalation paths that become visible only when multiple misconfigurations are considered simultaneously. Whether you’re responsible for defending enterprise environments or assessing them for risk, this talk will provide new insight into how AD CS misconfigurations can be weaponized in combination and how to detect and mitigate these risks before they’re exploited.